Your cart is currently empty!
Category: News

As IT environments grow more complex, IT professionals are facing unprecedented pressure to secure business-critical data. With hybrid work the new standard and cloud adoption on the rise, data is increasingly distributed across different environments, providers and locations, expanding the attack surface for emerging cyberthreats. While the need for a strong data protection strategy has…

Mar 13, 2025Ravie LakshmananAuthentication / Vulnerability Two high-severity security flaws have been disclosed in the open-source ruby-saml library that could allow malicious actors to bypass Security Assertion Markup Language (SAML) authentication protections. SAML is an XML-based markup language and open-standard used for exchanging authentication and authorization data between parties, enabling features like single sign-on (SSO),…

Most microsegmentation projects fail before they even get off the ground—too complex, too slow, too disruptive. But Andelyn Biosciences proved it doesn’t have to be that way. Microsegmentation: The Missing Piece in Zero Trust Security Security teams today are under constant pressure to defend against increasingly sophisticated cyber threats. Perimeter-based defenses alone can no longer…

Mar 14, 2025Ravie LakshmananMobile Security / Encryption The GSM Association (GSMA) has formally announced support for end-to-end encryption (E2EE) for securing messages sent via the Rich Communications Services (RCS) protocol, bringing much-needed security protections to cross-platform messages shared between Android and iOS platforms. To that end, the new GSMA specifications for RCS include E2EE based…

The North Korea-linked threat actor known as ScarCruft is said to have been behind a never-before-seen Android surveillance tool named KoSpy targeting Korean and English-speaking users. Lookout, which shared details of the malware campaign, said the earliest versions date back to March 2022. The most recent samples were flagged in March 2024. It’s not clear…
![Microsoft Warns of ClickFix Phishing Campaign Targeting Hospitality Sector via Fake Booking[.]com Emails](https://itdisasterfixes.com/wp/wp-content/uploads/2025/03/wp-header-logo-81.png)
Microsoft has shed light on an ongoing phishing campaign that targeted the hospitality sector by impersonating online travel agency Booking.com using an increasingly popular social engineering technique called ClickFix to deliver credential-stealing malware. The activity, the tech giant said, started in December 2024 and operates with the end goal of conducting financial fraud and theft.…
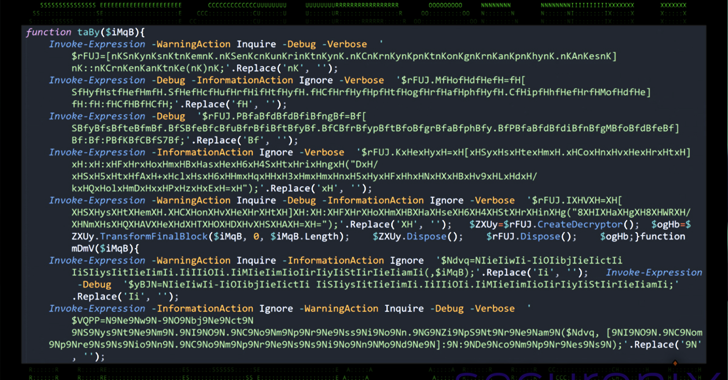
Mar 14, 2025Ravie LakshmananThreat Intelligence / Malware A new malware campaign has been observed leveraging social engineering tactics to deliver an open-source rootkit called r77. The activity, condemned OBSCURE#BAT by Securonix, enables threat actors to establish persistence and evade detection on compromised systems. It’s currently not known who is behind the campaign. The rootkit “has…

Mar 14, 2025Ravie LakshmananSoftware Security / Cybercrime Users searching for pirated software are the target of a new malware campaign that delivers a previously undocumented clipper malware called MassJacker, according to findings from CyberArk. Clipper malware is a type of cryware (as coined by Microsoft) that’s designed to monitor a victim’s clipboard content and facilitate…
Mar 14, 2025The Hacker NewsData Protection / Ransomware Cyber threats evolve daily. In this live webinar, learn exactly how ransomware attacks unfold—from the initial breach to the moment hackers demand payment. Join Joseph Carson, Delinea’s Chief Security Scientist and Advisory CISO, who brings 25 years of enterprise security expertise. Through a live demonstration, he will…

Mar 14, 2025Ravie LakshmananCybercrime / Ransomware A 51-year-old dual Russian and Israeli national who is alleged to be a developer of the LockBit ransomware group has been extradited to the United States, nearly three months after he was formally charged in connection with the e-crime scheme. Rostislav Panev was previously arrested in Israel in August…
